Your first touchpoint with the infrastructure of blockchain technology will be learning in-depth about the elements and participants of it (i.e., miners, nodes, hash functions, public-key cryptography, digital signatures and addresses).
The blockchain documents every transfer of money made within a certain network (e.g., the Bitcoin network). This ensures that no one can spend the same set of their money twice. Through this, blockchains managed to solve the so-called double spend problem in the digital world. Instead of sending out copies of one original item or asset, blockchains enable digital things to exist in only one location at a certain moment in time. Digital money and assets would not be operable if a copy of that money or asset could be sent twice.

The nodes which are a network of computers, run a blockchain and form its core infrastructure. Nodes in the network are exchanging information on new incoming transactions and the formation of blocks. It is important to note that there exist different types of nodes. A full node is a node that maintains a full copy of the blockchain and has offline capabilities whereas a light node does not keep a copy of the blockchain and is more limited in its functionalities (i.e., it only downloads the block header instead of the complete block). Before a light node can be part of a blockchain network (i.e., to send or validate transactions), it needs to be connected to a full node. In this sense, the blockchain network is similar to the infrastructure supporting your phone.
Full nodes can be compared to the cell phone tower that your phone (i.e., the light node) is connecting to. All the antenna stations (i.e., full nodes) – are connected to each other and make up the communication network infrastructure. If you want to make a call with your phone, you need to connect to a cell phone tower first before you can interact with any other mobile phone. Similarly, in the distributed network of a blockchain, the full nodes are up and running most of the time and make up the distributed network. They also maintain a copy of the entire blockchain. You are likely to use a light node if you use a wallet on your phone or computer. In this case, you are going to connect to a full node first before you can interact with the blockchain. Participants of a network decide to run a full node if they want to contribute to the stability and security of the network, but to use cryptocurrencies it is not a necessity.
Every miner is a node in the blockchain network but you do not need to be a miner to run a node. Miners support the network by forwarding information and maintaining a copy of the blockchain, just like all the other nodes. As opposed to non-miner nodes, miners are responsible for creating new blocks in the chain of blocks. Each block in a blockchain is a collective decision on the history of a given point in time. To find a collective decision, the network finds a consensus on which transactions are included in the next block and in which sequence. Not all proposed blocks by miners are the same. One reason for that is that it takes differing amounts of time for new transactions to spread across the entire network, causing differing transaction pools of unverified transactions to gather.
In Ethereum, miners are called validators since Ethereum switched from its Proof-of-Work to the Proof-of-Stake algorithm. A validator is essentially a voter for a new block. The more votes a block receives, the more likely it is that it will be chosen.
The reason why miners have an interest in acting honestly and in the interest of the network is because they are incentivized to behave according to the rules of the blockchain. If an invalid transaction is put into a block, this block has no chance of being the winning block given its faulty data entry. The miner solving the puzzle first is rewarded with the block rewards and/ or the transaction fee that anyone sending a transaction via the Bitcoin and Ethereum blockchain has to pay in order for the transaction to be included in one of the next blocks.
The probabilistic chance to receive the block reward and the transaction fees creates the incentive for individuals to purchase and run the costly hardware needed to solve the cryptographic puzzle. The first miner to solve a block receives a reward in the currency that she is mining. The winning miner is allowed to send themselves a transaction with a few coins (depending on the blockchain and cryptocurrency) that did not exist before.
Miners receive the final batch of transaction data, which is then run through a cryptographic algorithm. During this process, a hash, a string of numbers and letters that does not reveal any transaction data, is generated and used to verify validity. The hash ensures that the corresponding block has not been subject to changes. If even one number is off or out of place, the corresponding data generates a different hash. The hash of the previous block is integrated into the next block, so that if anything has been changed in the previous block, the generated hash will change. The hash value must also be below a target value set by the hash algorithm. If the generated hash value is too large, it is generated again until it is below the specified target value.

Data verification is an important component when building a data structure on a decentralized network. Only through verification, can participants distinguish between valid data and invalid information. In blockchain systems, hash functions are the mathematical one-way function used as a means to verify data in blockchains at different stages of a data verification (i.e., when creating an address, proving ownership, proving the integrity of the blockchain itself).
All hash functions take inputs of variable length and produce an output of fixed length called the hash value. Has functions are irreversible one-way functions. You cannot translate your hash
back into the data that you put in to receive the hash value as was shown in the blockchain demo video. Hash functions are pseudo-random (i.e., they produce seemingly random outputs from two similar inputs). The likelihood of a hash function producing the same output for two or more different inputs is highly unlikely. However, they are deterministic meaning that they always produce the same output from a specific input. In this sense, a hash value is similar to a fingerprint of data. One can verify the integrity of files and detect changes by comparing their hashes. The input can be any type of data (i.e., audio, video, picture) it is not restricted to numbers.
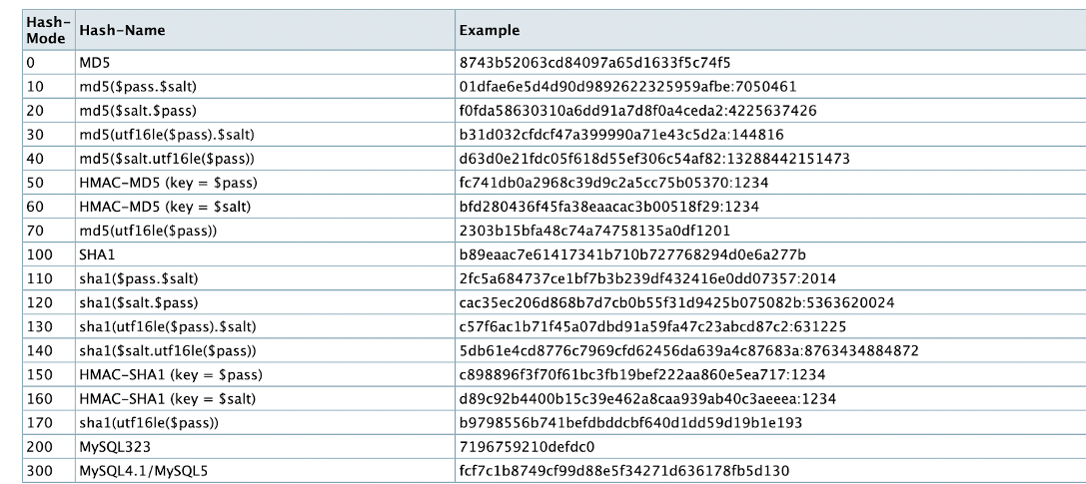
Figure 5: Generic hash types (Source: Hashcat, accessed on 15.11.2022)
As the figure shows, there are different hash functions that have different fixed-length outcomes and are used by different blockchains. One of the most commonly used hash functions is the so-called SHA256 (Secure Hash Algorithm 256 bit). The 256 stands for the fixed length of the hash value. There are many hash functions, most of which indicate their fixed length in their name.
Public-Key Cryptography (also known as asymmetric cryptography) grants cryptocurrency holders access to their funds. It offers a way to prove ownership. In symmetric cryptography, you encrypt and decrypt a message with the same key from both ends. This works similarly to a padlock where you use the same key to open (decrypt) and close (encrypt) the padlock. Asymmetric encryption stems from the property of keys always coming in pairs and being used complementary. One of the keys encrypts something and the other one decrypts it. The keys are called public key and private key, also spending key or secret key. Your keys translate to your identity on the blockchain. You receive funds with your public key and send funds with your private key.
Keys and Identity
The idea in cryptocurrencies is that you are receiving funds with your public key and spending them with your private key. The keys are named public and private on purpose since you can share your public key with everyone. You need your private key to spend your funds. Whoever has access to your keys, can access your funds. A public key is similar to your address. You can give it to people that want to send you a letter or package. Your private key is like the key to your postbox. Only this key lets you access your mail and usually, only you have access to it. Your keys are needed for both, sending and receiving transactions. A transaction is on a technical level a message to all nodes in the network. The information in the message is then encrypted via the private keys which are called signing a transaction digitally. This process is not done manually instead, there are wallets that do these steps for the user. Wallets are able to generate and manage keys and encrypt and decrypt.

Generating Keys and Addresses
Funds or data which is sent to a public key can only be accessed by those in possession of the corresponding private key. The public key is derived from the private key via Elliptic Curve Cryptography (ECC). ECC is the most commonly used public-key cryptography scheme in cryptocurrencies, though there are other cryptographic schemes. Cryptography uses one-way functions, and multiplication on an elliptic curve is another one-way function of note. Thus, the derivation of a public key from a private key cannot be reversed.
Digital Signatures
A transaction can only be validated if it has a valid digital signature. The private key associated with the address storing the funds has to sign a transaction.
When a transaction is broadcast to the network, all full nodes and miners verify it based on the message, public key or address, and signature. A signature can only be valid or invalid at the end of the verification.
Peer-to-Peer Network
In a P2P network all participants have the same role. Each of them acts as a client (i.e., requesting data) and as a server (i.e., providing data). The advantage of a P2P network is that if one machine becomes unavailable, the machines that are still connected to the network continue to provide services. This system architecture makes blockchain networks resilient to single-points-of-failure.
Mining & Consensus
Every blockchain must choose a mechanism that ensures all participants agree on a single truth regarding the data. Think of it as a standardized way to get all the politicians in a parliament to agree on an opinion as quickly as possible. Since the politicians probably need to discuss it, all participants in a blockchain network also do so by communicating with each other through the network. The communication protocols are implemented in the software that is executed on all participating devices. However, communication is not about a political opinion, but about the data status of the blockchain, such as the transaction history of a currency like Bitcoin. To resolve this issue in blockchain networks, a consensus mechanism is used.
The Problem of the Byzantine Generals
The various consensus mechanisms solve an ancient problem, referred to as the Byzantine generals’ problem. The initial dilemma is the following:
A queen is trapped in her castle with her 500 soldiers because the castle is besieged by five armies, each 100 strong. Each army has set up camp near the castle and is under the independent command of one general from each army. The generals must communicate with one another to find agreement on an attack strategy. However, their trust in one another is limited because they suspect that some of them are traitors. If the generals would send a message laying out the tactics and timing of the attack by a messenger from camp to camp, generals loyal to the queen could easily make changes to the message and thus pass false information to the next camp.
Consequently, the alteration of written messages is not a secure means of communication. The spread of misinformation could lead to the victory of the malicious generals given that different camps would not attack simultaneously or not at all. In the 21st century, the basic problem still remains: How can one be sure that a message is authentic and has not been subject to changes and malicious activity?
Authenticity refers to the certainty that counterparties did not forge calls and emails or pretend to be someone else. Tampering means the distortion, deletion, or viewing of the message by malicious parties.

To solve the problem of Byzantine generals, consensus mechanisms are based on two concepts:
All generals must first have skin in the game by contributing something to the network that they would not get back in case they behave against the rules. For example, imagine two businessmen who want to start a joint venture, but one of them refuses to invest time or capital. The other businessman who has skin in the game would question the loyalty of the other. This can be applied to decentralized networks.
Secondly, the ledger has to be manipulation-free (referring to past and present transactions). A system is tamper-free if the nodes in the network immediately detect any change or deletion of previous transactions and data. All user transactions are recorded, verified and stored on a blockchain.

In the case of the Byzantine generals, one solution could be to let generals pay a high sum up front as a token of their loyalty. Before a general can pass on a message, their identity would need to be proven by a cryptographically secured and unique signature. If one general is sabotaging the attack, the transaction history can give information on the identity of the individual giving the signature. The punishment for maliciousness is financial loss for the general since they are not reimbursed for the deposit made upfront. Reaching consensus in this way is called 'proof-of-stake'. All generals have invested a stake in maintaining the network upfront to participate. Another alternative would be for each general to solve a complex math problem before signing and sending a message is permitted. The general would need to pay a lot of money to workers solving the math problems for them. This method is referred to as Proof of work (PoW). Each general proves his loyalty to the network by consuming costly and time-consuming resources.
Consensus in Distributed Systems
The history of cryptocurrencies, the order in which transactions were validated is crucial to be kept track of. When a network participant creates a transaction, the transaction is broadcast to the entire network. Each node records the new transactions and adds them to its version of the ledger. The versions of the
ledger differ slightly from one to the other. If a node is based in the EU and broadcasts a transaction, the nodes that are closest to it receive it earlier than a node based in the US. This results in slightly different versions of the same transaction history. Eventually, all network nodes need to agree on a given order and this is what the consensus mechanism of a blockchain achieves. There are many approaches to reach consensus in a distributed network, the two most prominent ones are the PoW and Proof of Stake (PoS) algorithms.
Proof of Work
The term "mining" is known from Bitcoin, for example. The Ethereum network used to run on PoW as a consensus mechanism transactions have to be packaged into blocks by means of mining and thus confirmed. PoW describes the condition that a participant in the network must have performed honest and provable work in order to confirm a number of transactions. The block reward which miners receive is intended to compensate for the electrical energy expended and the use of special hardware (e.g., ASIC miner or GPU), and beyond that to make a profit from the current block reward and the transaction fees approved in the transactions. PoW is the most widely used method in cryptocurrencies so far. The high stakes involved in mining also ensure that the coins generated through it have a real equivalent value in the form of fiat money.

As robust and proven as the process may be, it is also heavily criticized. The downside of PoW is the usage of electrical energy and the sometimes specially manufactured hardware is consumed at the expense of the environment. The comparison (based on ballpark number estimates) to frequently used services and industries (e.g., Netflix, YouTube) and Bitcoin and Ethereum energy consumption levels puts the energy usage of PoW and PoS into perspective.
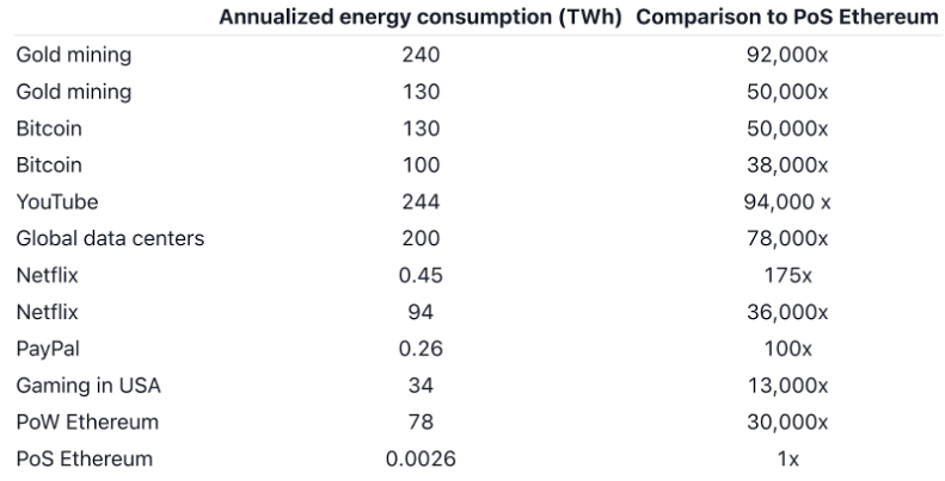
Figure 6: Comparison of annualized energy consumption of services and industries
(Source: Ethereum's energy expenditure, Ethereum Foundation, 2022)

Estimates of YouTube's energy expenditure have also been broken down by channel and individual videos. Those estimates show YouTube used over 175 times more energy watching Gangnam Style in 2019 than Ethereum uses per year.
Ethereum Foundation, 2022

While the reduction of the carbon footprint of crypto (by use of renewable energy sources) is desirable, one must answer the following question for themselves:
Are the functions that Bitcoin and other cryptocurrencies fulfill worth the energy expenditure that they incur?
Another disadvantage is the division of the community of these projects. There are always two groups. Users, who have to raise the transaction fees and wait for the confirmations, and miners, who have their eye on profit and mostly want to make a political profit on the project for themselves. Suggestions on how to improve the project and its source code implementation usually trigger discussions in which both camps vigorously defend their own interests.
Proof of Stake
As in a stock corporation, for example, in PoS all shareholders have the right to have a say in the consensus. This entitlement to validate a block of new transactions is deterministically (by pseudo-randomness) assigned each time. In this process, shareholders with more assets in their wallets have a slightly higher chance of being selected. On the one hand, they have a higher interest in the functionality of the network and should therefore contribute relatively more. On the other hand, with too heterogeneous a selection of shareholders comes the risk that block confirmations become centralized and empower parties holding large shares of the asset, resulting in an unfair redistribution of wealth. In most cases, in PoS-based blockchains, the corresponding tokens are already "pre-mined" (i.e., created) instead of being slowly flushed to the market through block discovery until the set maximum is reached, as in PoW. PoS blockchains thus, usually already have all shares in circulation and can only pay shareholders who win blocks with transaction fees. Energy consumption is limited to simple use by the participants and is not driven up by complex calculations as it is in PoW consensus mechanisms.
